From a reconnaissance point of view there isn't much to do excepting noting down the IP address of the machine. You can also download this room as a virtual disk file and run it upon an instance of VirtualBox or VMware. Another thing that you must be mindful of is that the machine takes some time to boot so try pinging it before moving on with a nmap scan.
I went ahead with a aggressive scan while also utiltizing the nmap's scripting engine to fire up the scripts in vuln category. The command being nmap -n -Pn -T5 -A --script=vuln <IP_Address> wherein the arugments are
- -n: To turn off DNS resolution
- -Pn: To not ping the IP address and directly go ahead with scanning it as I knew if was alive
- -T5: To increase the timing speed to maximum
- -A: To perform an aggressive scan which is a combination of custom scripts, OS fingerprinting and service detection of the ports
- --script=vuln: This is a group of nmap scripts which are used to scan the target for potential vulnerabilities
1. Scan the machine - Done
2. How many ports are open with a port number under 1000? - 3 which are 135 (msrpc), 139 (netbios-ssn) and 445 (microsoft-ds)
3. What is this machine vulnerable to? - ms17-010 which is conveniently provided to us under the heading of vulnerable. If you google about this vulnerability you'll come up with its name which is eternalblue hence the name of this machine.
EXPLOITATION
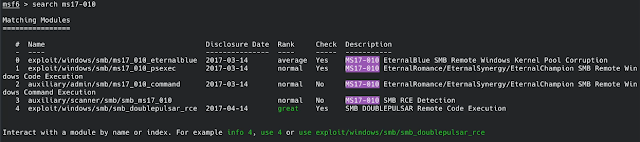
Since we know what the vulnerability is, the next step is to exploit it with metasploit. Use the search command to look for modules which could help us in leveraging it to gain a shell on the system.
We can use the first exploit here named exploit/windows/smb/ms17_010_eternalblue. Use it and execute the show options command to take a look at the fields which need to be modified. The only field which needs to be filled is RHOST which takes the IP address of the machine. Before running this module we need to manually define the payload for it and tryhackme suggests a simple command shell for it which can be accessed with the module named windows/x64/shell/reverse_tcp. However a better option would be to use a more capable shell program such as meterpreter which can be used with the following module windows/x64/meterpreter/reverse_tcp.
So once you've selected your payload of choice its time to run the exploit, sit back and watch the magic. At this point we have also completed our Task 2:
- Start Metasploit - done with the command msfconsole
- Find the exploitation code we will run against the machine - exploit/windows/smb/ms17_010 which was discovered with the help of search command
- Show options and set the one required value - RHOSTS was the only one that needed to be filled
- With that done, run the exploit! - done with the run command
- Confirm that the exploit has run correctly - done when we get back our shell
POST EXPLOITATION
Task 4 has been completed
- If you haven't already, background the previously gained shell - done with background or Ctrl + Z
- What option are we required to change? - session
- Set the required option, you may need to list all of the sessions to find your target here - done with sessions -i
- Run - done with run command
- Once the meterpreter shell conversion completes, select that session for use - done with sessions -i <session_id>
- Verify that we have escalated to NT AUTHORITY\SYSTEM - done with getuid command
- List all of the processes running via the 'ps' command. Find a process that is running at NT AUTHORITY\SYSTEM - done
- Migrate to this process - done with the command migrate <process_id>
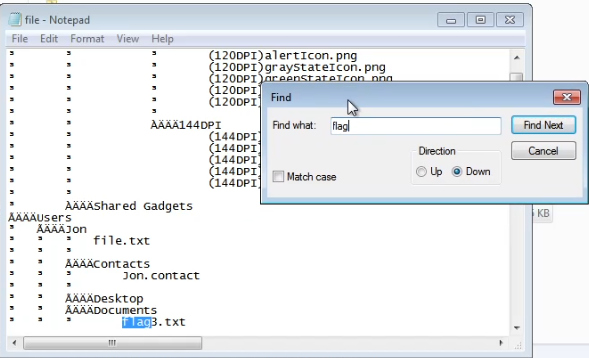
- What is the name of the non-default user? - Jon
- What is the cracked password? - alqfna22




Comments
Post a Comment